Securing Your First Connected Device - A First-Principles Breakdown Your Non-Tech Friends Will Actually Understand
(How pocket calculators and smart cars stay secure—and how to build yours right).
Over the past decade of designing, testing, and riding India’s first connected electric scooter, our team has fought every gremlin that sneaks into hardware—from loose screws to rogue firmware and cloud quirks. We learned the hard way that building physical products isn’t just about elegant circuits or sleek plastics; it’s about protecting every bolt of data that flows through them. This post distills those lessons into a single, high-level guide: the security pitfalls we tripped over, the fixes that finally stuck, and the mind-sets that kept us sane. Whether you’re hacking on a pocket calculator, a smart helmet, or the next two-wheeler that will change city streets, we hope these notes save you from reinventing the wheel—or worse, watching it roll away.
Imagine every connected device you own - a QR-code-printing calculator at the corner store, the smart scooter you weave through traffic, your car that streams over 5G. All of them are, at heart, tiny computers that speak to bigger computers on the cloud. Once wireless linking between these systems and payment gateways enter into the picture, “computer security” suddenly is extended to include physical locks, cryptography, factory processes, app design and even what text should appear on the screen.
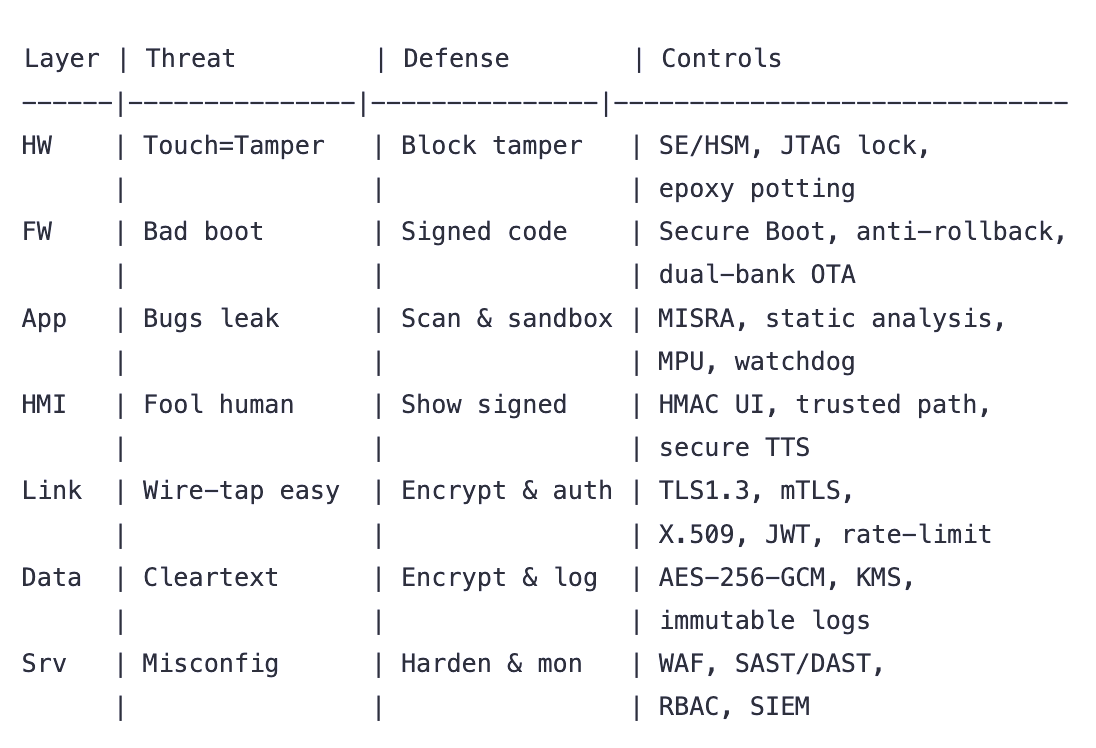
Below is a guided walkthrough - layer by layer - of what can go wrong and how good engineers make it hard for the bad guys to win. You will see seven layers (Hardware → Firmware → On-Device App → Human Machine Interface → Cloud Connection → Data → Server-side App), the common type of attack faced by each layer, and the typical “seats and airbags” that keep the users safe.
But first let me talk about why Severity and Occurrence (or Real-World frequency) matters, or let me put it in another way…
Why “How Bad” & “How Often” Both Matter
Think of severity like the size of an explosion. If a single bicycle's paddock snaps, one rider is stranded - that's like a fire cracker. But if the thief steals the factory’s master key, every bicycle on the street is up for grabs - that’s dynamite. The bigger the room, the faster you need to act.
Now think of occurrence as how often those blasts go off. Tiny firecrackers—loose passwords, data sent in plain text—pop and fizzle almost daily. They’re small, but the constant bang-bang can still scorch the whole warehouse if nobody bothers to sweep up the sparks. A stick of dynamite—the Black-Mirror-grade side-channel hack—detonates only once in a blue moon, yet its shockwave can flatten every wall you’ve built.
Seasoned engineers act like bomb-squad captains. First, they snuff out the firecrackers that go off all the time: replace default logins, turn on encryption, patch the holes. With the nightly pops under control, they reinforce the walls and bolt the vault for that rare, earth-shaking blast—adding tamper-proof chips, shielding circuits from snoops, and double-locking the master key.
Now that this is clear, let's dive into the layers one by one, just like an attacker would.
Why attackers bother
If you can open it, you can own it. Removing chips, probing test pins or reading electrical noise lets a determined attacker steal secret keys or clone the entire product.
Seatbelts and Airbags
Tamper-evident casings, secure elements (little vault chips that never reveal secrets), and fusing off debug ports mean that prying open the device leaves visible scars - or no data at all.
Severity: High. Steal one secret, break every device
Occurrence: Moderate. Mostly in high value gadgets like POS terminals and vehicles
Why are the good guys bothered?
Flash the wrong firmware and the car may snitch on your every ride, disable the speed cap, or brick itself - one file (or binary) can hijack the whole fleet.
How do the Engineers fight back?
Engineers counter with Secure Boot (a fancy word for a chip that checks a cryptographic “passport” before any code runs) and anti-rollback rules that refuse older, buggy versions. Signed, encrypted Over The Air updates - and a read-only backup image - add extra layers of protection
Severity: High (a single compromise scales to thousands of devices)
Occurrence: Moderate. Botched updates and hobbyist/enthusiast/tech-bro tweaks show up regularly, full blown attacks less so but still very real.
What tempts the attacker?
Picture the software running on your phone as a helpful cashier. If the cashier is careless - scribbling totals on napkins and never double-checking any orders - any con-artist can sweet talk their way into free food or cash. In tech terms, sloppy input handling, buffer overflows, or unchecked privileges in the embedded application layer lets thieves leak credit card information or send absurd commands like “refund $100” (logic manipulation, memory corruption, privilege escalation).
How the Engineers stay ahead of trouble
They give the cashiers strict book-keeping lessons called secure-coding standards/practices. Every new line is run through an automated spell-checker - static and dynamic analysis tools that yell the moment they spot a potential scam. Valuables locked behind the fence - Memory Protection Unit(MPU) keeps secret keys and user data in their own vault. Finally an overlord or robotic supervisor - watchdog - kicks in if the program behaves oddly. The watchdog also sends this behaviour to HQ for forensics.
Severity: High. One rouge app can steal funds or crash the entire fleet of devices in minutes.
Occurrence: Common. Coding mistakes creep in every release cycle, especially if there are multiple systems in play. While full scale exploits are very rare, bug bounty programs show that they are discovered in the wild every year.
What tempts an attacker?
When Engineers do a great job on their systems, Hackers turn to the un-informed/unaware end user. These crooked operators rig the weight scale to show 1 kg while actually charging for 10.
Similarly, hackers spoof displays or hijack speaker prompts so that when you approve for $100, but pay $1000. These tricks rely on UI Spoofing and input-injection techniques that are aimed to mislead rather than tamper with the machine/system.
What do the Engineers do to get ahead ?
First, The Face displays numbers only if the bank has signed them - server‑signed UI data (think tamper proof price tags). The entire display module is bolted onto a purposeful cage - swapping the displays or even removing it will leave unmistakable scars(temper-evident bezel). Audio receipts such as “received one hundred rupees” are generated from a message that carries its own cryptographic autograph(authenticated TTS Payloads), so even if someone plays ventriloquist, the device can tell it’s fake.
Severity: Medium. Successful scams usually target a single user per incident, but repeated frauds wreck customer trust and may trigger hefty fines
Occurrence: Occasional. Physical access or elaborate phishing setups are required, so attacks surface less often than pure network hacks but still appear in retail POS fraud reports worldwide.
What tempts an attacker?
Imagine shouting your ATM PIN across a crowded railway platform. Anyone within earshot will swipe it. The same happens if your device speaks over plain text. The same happens if your device speaks over plain-text MQTT or HTTP(communication protocols). A bystander sniffs traffic, steals credentials, or performs a man-in-the-middle trick to reroute payments.
What do the Engineers do to get ahead ?
They make every conversation a secret-handshake club. Devices and servers exchange digital passports via Mutual TLS(mTLS). Without both stamps, the gate stays shut. Even after entry, keys behave like single-ride metro tickets: JWT/OAuth tokens expire quickly and rotate automatically, negating the stolen copies. To catch brute-force trespassers, connection attempts are counted and throttled, while smart alarms(anomaly-detection scripts) flag bursts of weird log-ins for analysts.
Severity: High. A hacked session can lead to money being re-routed and/or fake firmwares being deployed at scale
Occurrence: Occasional. Physical access or elaborate phishing setups are required, so attacks surface less often than pure network hacks but still appear in retail POS fraud reports worldwide.
What tempts an attacker?
Data is the new gold: transaction histories, inventory numbers, user IDs. If a thief grabs the hard drive - or intercepts a wireless packet - they can fence that gold on the dark market(web), forge refunds, or blackmail. Threats include data-at-rest theft, in-transit interception, and SQL/NoSQL injection.
What do the Engineers do to get ahead ?
Every dairy entry is written invisible in - AES-256 encryption at rest - so stealing the notebook yields gibberish. Messages travel in locked briefcases:TLS 1.3 keeps spies from peeking mid-air. Inside the warehouse, guards check ID - fine-grained database roles and policies ensure a calculator's firmware can't rummage through tomorrow’s scooter analytics. Continuous backups and immutability logs let responders rewind time if the vandals tamper with records.
Severity: High. Leaked personal or financial data triggers lawsuits, regulatory fines and brand erosion over night.
Occurrence: Common. Weak storage settings, shared credentials, or mis-set rules appear in breach disclosures year after year.
What tempts an attacker?
Why steal a few bicycles when you can steal the factory? Cloud APIs command every device - compromise them and you rewrite the rulebook for an entire product line. Common ploys: injection attacks, over privileged admin accounts, and vulnerable third party libraries.
What do the Engineers do to get ahead ?
A Web Application Firewall filters every incoming request like airport security. Code is scanned continuously in the CI/CD conveyor belt with SAST/DAST tools, catching flaws before deployment. Permissions follow a military chart - Role-Based Access Control (RBAC)- so interns can't drop production databases. Finally an always-awake control tower (SIEM platform) watches logs and triggers a rehearsed incident-response plan whenever alarms blare at 3am.
Severity: High. A single API breach can broadcast malicious commands to thousands of calculators, scooters, or cars simultaneously.
Occurrence: Common. Headlines show new cloud mis-configurations almost monthly. Forgotten admin passwords and outdated frameworks remain favorite hacker entry points.
Pulling it all Together
Final Take-Aways for Builders and Buyers
Layered security beats silver bullets. Assume one layer will fail; another should be able to catch the fall.
Start at the factory. A secure boot chain or unique certificate burned in production is worth a thousand post‑launch patches.
Design for seamless updates. Bugs are inevitable—secure, painless OTA updates will let you fix them quickly.
Watch real‑world data. Logs and alerts turn “unknown unknowns” into “spotted and stopped.”
Use industry standards. They condense decades of painful lessons into checklists you can adopt to today.
Whether you’re shipping a smart calculator that prints receipts, a connected scooter zipping through Bangalore, or the next software‑defined car, following these first principles keeps your customers’ money, movement, and peace of mind exactly where they belong.